This is my 3rd Part on installing and configuring Active Directory domain controller using PowerShell DSC (Desired State Configuration), Earlier in Part 1 : Install and configure AD using GUI way, and in the Part 2 : Normal PowerShell commands are used to do the same task.
Powershell DSC (Desired state configuration) is a very cool method of performing task remotely. I am seeing over the period Microsoft is evolving its script technology to make life more hassle free for remote management
What is DSC (Desired State configuration)?
In my words DSC uses WS-Management protocol (WinRM) it made to push configuration on remote server or pull information from DSC server. (To see how i enabled WinRM service please check my blog Method 5 PowerShell Remoting) Once you run DSC command you are telling remote computer that its configuration must be according what I am defining. Prerequisite to use DSC is your computers should have at least PowerShell Version 4. That version is there by default there on windows 2012 and windows 8 and above.
My script is based on this Microsoft article which for running script locally on the server. I am showing how to configure it remotely, As I am going to use DSC between my desktop and windows server 2012 R2, They are not in domain. (I don't have any Active directory yet). I will need to configure PSRemoting first. I wrote separate article on how to configure PSRemoting in workgroup computers and it is most essential part. Next is to install xActiveDirectory module from internet, Open Powershell as administrator, and fire command Install-Module xActiveDirectory -Force. It contacts online repository and download required modules.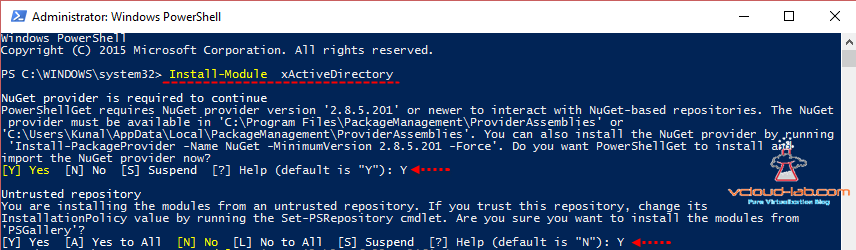
Once Module is downloaded it will be stored at location "C:\Program Files\WindowsPowerShell\Modules", It can be verified that I have module installed correctly by running below two commands.
Get-Module -ListAvailable -FullyQualifiedname xActiveDirectory
Get-DscResource -Module xActiveDirectory
Same steps need to performed on remote server as well. (I already have all these things configured in my VMware Template in the first place, so every time I clone it I don't have to touch VM), Installing module or coping xActiveDirectory folder from Desktop to Server at same location. (If remote computer doesn't have module DSC scripts will fail with error THE POWERSHELL PROVIDER DOES NOT EXIST AT THE POWERSHELL MODULE PATH NOR IS IT REGISTERED AS A WMI PROVIDER and another error I faced was A NETBIOS DOMAIN NAME MUST BE SPECIFIED for non standard domain name) 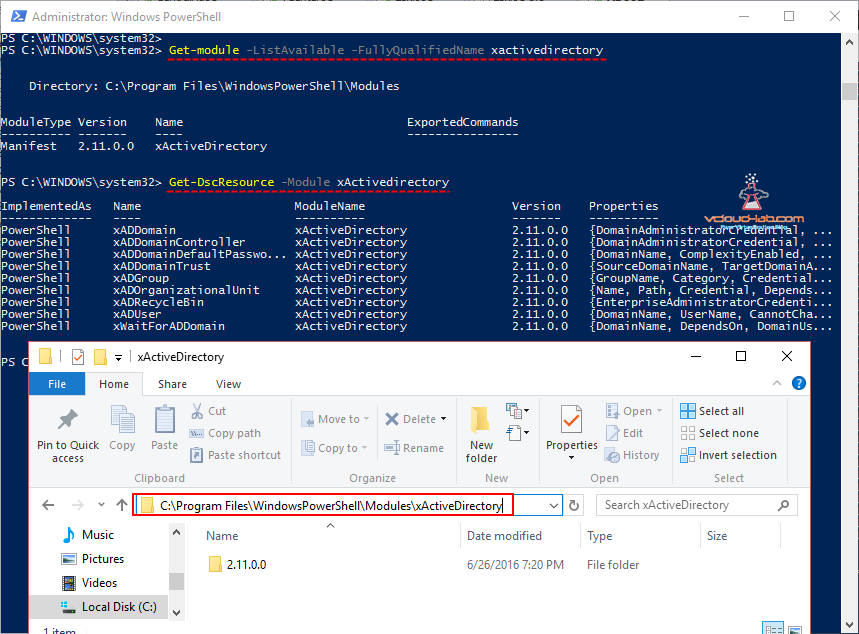
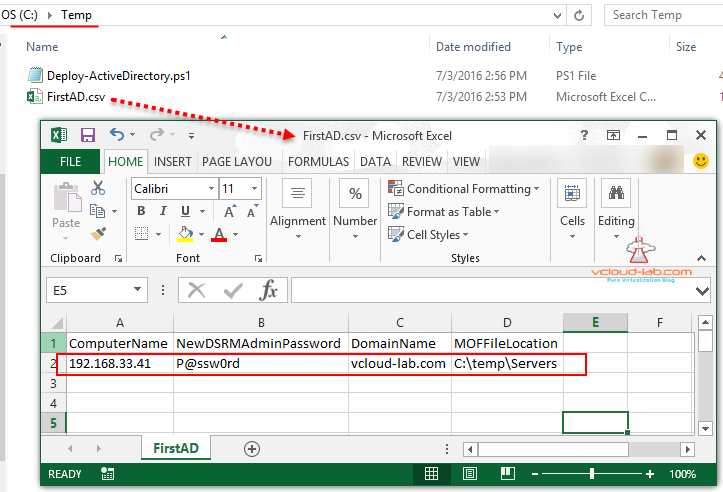
Next I have kept my script and information CSV file at c:\temp location. As I am running this in my lab environment passwords are not in clear text. (I recommend password encryption in production environment in Powershell DSC). I have Set-ExecutionPolicy Unrestricted -Force on my desktop, In CSV file one password I am using for DSRM (Directory service restore mode) as well as for Domain Administrator password.
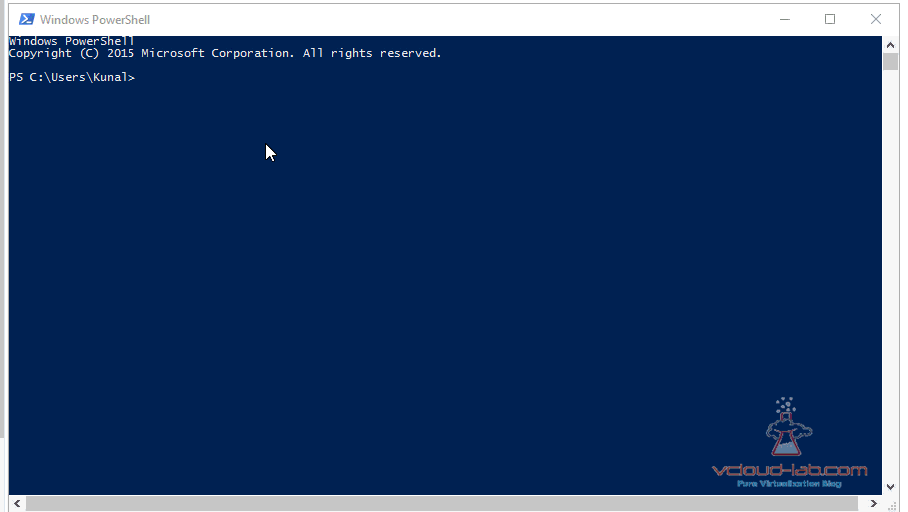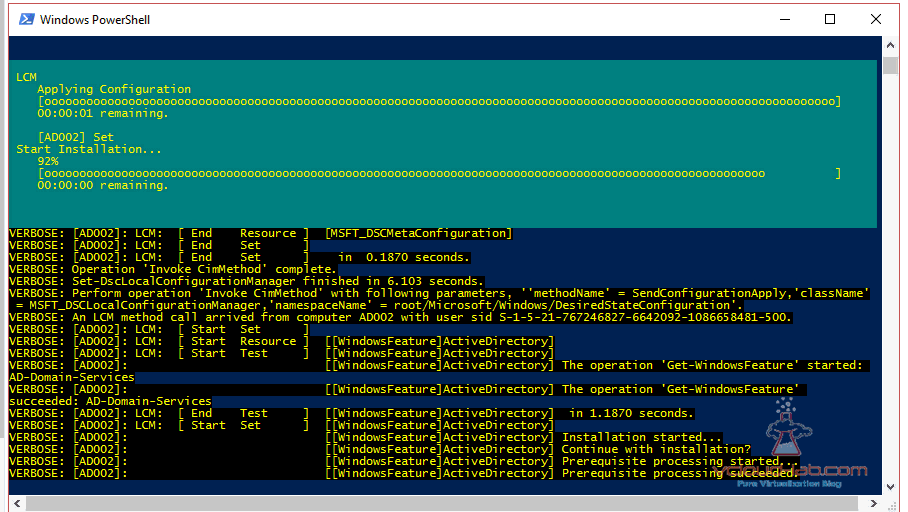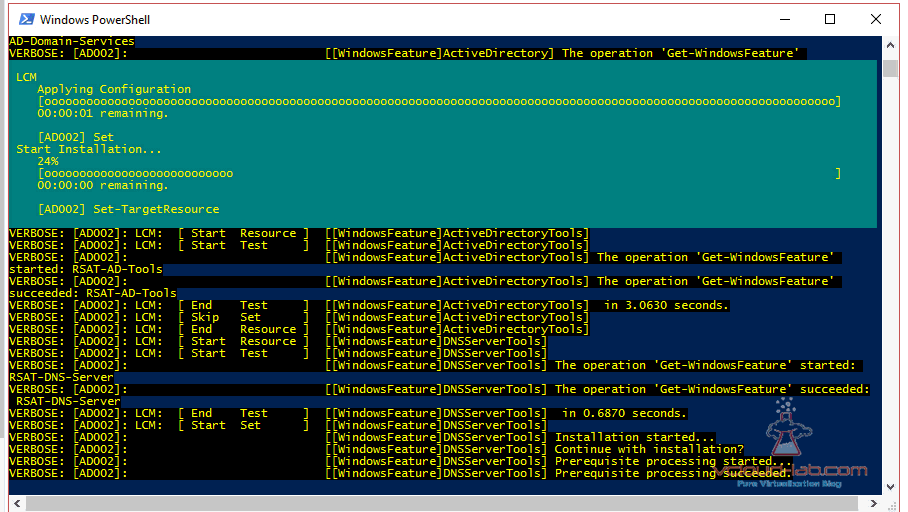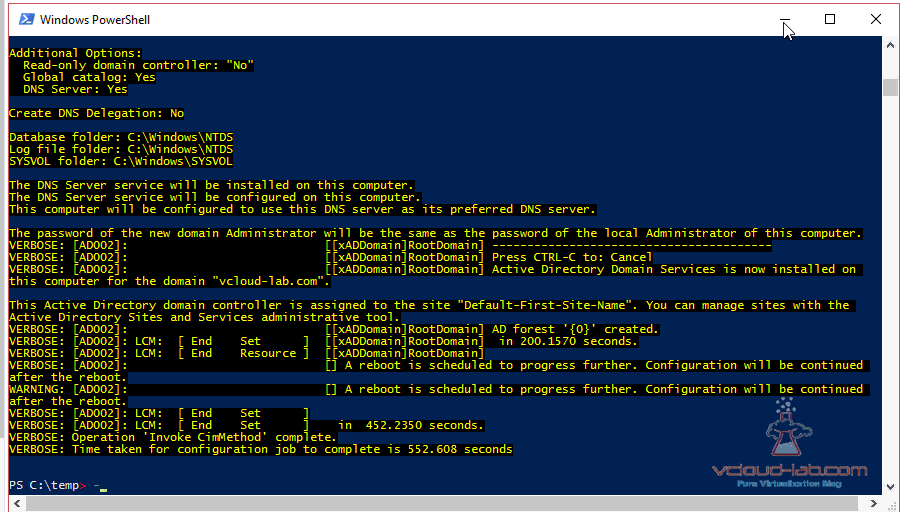
Next in the powershell I Set-Location (cd) to c:\temp, and run ps1 file as below animation. it will prompts for password to connect 192.168.33.41 (This is local administrator password)., When configuration part is executed it creates MOF file at same location I can use same MOF anytime I want, and within a couple of minutes I spin up new Active Directory domain controller for testing. you can download script and CSV file here. 
#Import configuration database from CSV file
$Data = Import-csv -Path c:\temp\FirstAD.csv
$ComputerName = $Data.ComputerName
$Password = $Data.NewDSRMAdminPassword
$DomainName = $Data.DomainName
$MOFfiles = $Data.MOFFileLocation
#Encrypt Passwords
$Cred = ConvertTo-SecureString -String $Password -Force -AsPlainText
$DomainCredential = New-Object System.Management.Automation.PSCredential ("$(($DomainName -split '\.')[0])\Administrator", $Cred)
$DSRMpassword = New-Object System.Management.Automation.PSCredential ('No UserName', $Cred)
#Create connection to remote computer
$RemoteAdministratorCred = Get-Credential -UserName Administrator -Message "$ComputerName Administrator password"
$CimSession = New-CimSession -ComputerName $ComputerName -Credential $RemoteAdministratorCred -Name $ComputerName
Configuration NewActiveDirectoryConfig {
param (
[Parameter(Mandatory)]
[PSCredential]$DomainCredential,
[Parameter(Mandatory)]
[PSCredential]$DSRMpassword
)
Import-DscResource –ModuleName xActiveDirectory
Node $ComputerName {
#Install Active Directory role and required tools
WindowsFeature ActiveDirectory {
Ensure = 'Present'
Name = 'AD-Domain-Services'
}
WindowsFeature ActiveDirectoryTools {
Ensure = 'Present'
Name = 'RSAT-AD-Tools'
DependsOn = "[WindowsFeature]ActiveDirectory"
}
WindowsFeature DNSServerTools {
Ensure = 'Present'
Name = 'RSAT-DNS-Server'
DependsOn = "[WindowsFeature]ActiveDirectoryTools"
}
WindowsFeature ActiveDirectoryPowershell {
Ensure = "Present"
Name = "RSAT-AD-PowerShell"
DependsOn = "[WindowsFeature]DNSServerTools"
}
#Configure Active Directory Role
xADDomain RootDomain {
Domainname = $DomainName
SafemodeAdministratorPassword = $DSRMpassword
DomainAdministratorCredential = $DomainCredential
#DomainNetbiosName = ($DomainName -split '\.')[0]
DependsOn = "[WindowsFeature]ActiveDirectory", "[WindowsFeature]ActiveDirectoryPowershell"
}
#LCM Configuration
LocalConfigurationManager {
ActionAfterReboot = 'ContinueConfiguration'
ConfigurationMode = 'ApplyOnly'
RebootNodeIfNeeded = $true
}
}
}
#Allow plain text password to be stored
$ConfigurationData = @{
AllNodes = @(
@{
NodeName = $ComputerName
PSDscAllowPlainTextPassword = $true
DomainName = $DomainName
}
)
}
#Generate mof files
NewActiveDirectoryConfig -DSRMpassword $DSRMpassword -DomainCredential $DomainCredential -OutputPath $MOFfiles -ConfigurationData $ConfigurationData
#Configure LCM on remote computer
Set-DSCLocalConfigurationManager -Path $MOFfiles –Verbose -CimSession $CimSession
#Start Deployment remotely
Start-DscConfiguration -Path $MOFfiles -Verbose -CimSession $CimSession -Wait -Force
Other useful blogs
PART 1 : POWERSHELL - CREATE LOCAL IIS WEB REPOSITORY FOR DSC MODULE
PART 2 : POWERSHELL - COPY DSC MODULE REMOTELY USING LOCAL WEB REPOSITORY
POWERSHELL: INSTALLING AND CONFIGURING ACTIVE DIRECTORY
POWERSHELL ACTIVE DIRECTORY: ADD OR UPDATE (CHANGE) MANAGER NAME IN ORGANIZATION TAB OF USER
POWERSHELL ACTIVE DIRECTORY: ADD OR UPDATE PROXYADDRESSES IN USER PROPERTIES ATTRIBUTE EDITOR
Powershell one liner: Create multiple user accounts
Active Directory Powershell: Create bulk users from CSV file