This is second part of configuring and architecting AD infrastructure new features. Microsoft has introduced new great feature with Windows Server 2016 Active directory, PAM (Privileged Access Management) Feature, Where user can be added to a group for a particular time. Once that Time to live (TTL) is expired account is automatically removed from group. This is the true automated way, and doesn't require much settings or any other third party software.
Prior to windows 2016 I wrote my own automation script, which was finding group, user and expiry date details from background SQL database and, my script was running in task scheduler continuously. With this feature it is gives more control now.
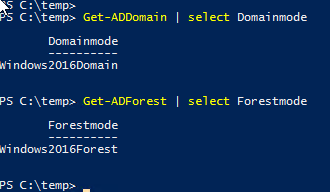
Before starting make sure you are on latest windows 2016 Domain and Forest functional level mode, Verify it using Get-Domain | select DomainMode and Get-ADForest | Select Forestmode. For another feature check Microsoft Active directory additional features - AD Recycle Bin Powershell.
This feature information can be viewed using below command. Note down DistinguishedName, It will be required in next one-liner command for configuration. EnabledScopes is empty, means feature is not configured yet and Requiredforestmode is matching my current forest functional level.
Get-ADOptionalFeature 'Privileged Access Management Feature'
Next command enables the feature on the forest level, I have used earlier info DistinguishedName as identity. This shows warning, that Enabling 'Privileged Access Management Feature' on 'CN=Partitions,CN=Configuration,DC=vcloud-lab,DC=com' is an irreversible action and you will not be able to disable if you proceed, If you agree press Y. (Make sure you have Enterprise admins and Schema Admins rights before proceeding)
Enable-ADOptionalFeature -Identity 'CN=Privileged Access Management Feature,CN=Optional Features,CN=Directory Service,CN=Windows NT,CN=Services,CN=Configuration,DC=vcloud-lab,DC=com' -Scope ForestOrConfigurationSet -Target vcloud-lab.com
If I use see the feature information again EnabledScopes attributes is no longer empty.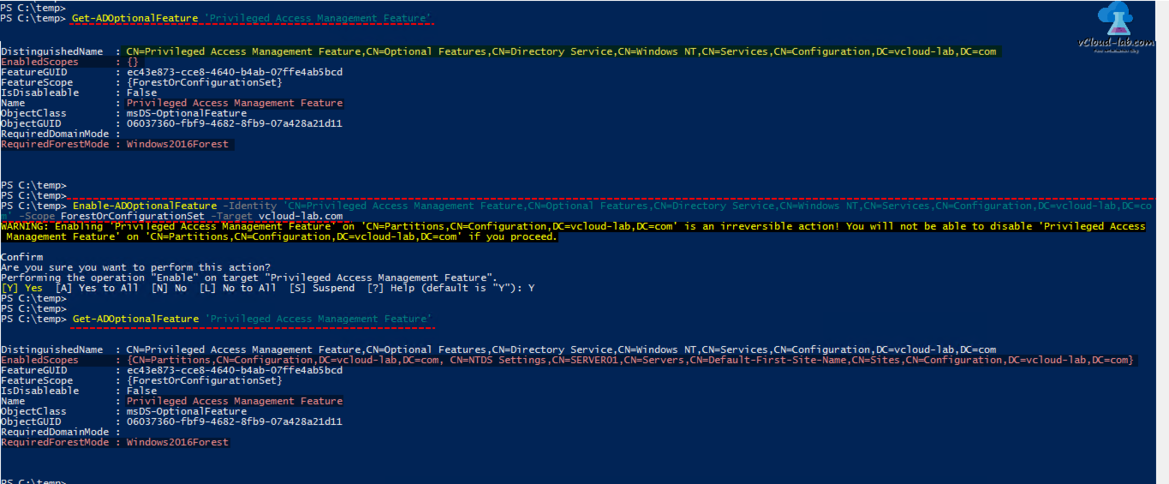
"The New-TimeSpan cmdlet creates a TimeSpan object that represents a time interval. You can use a TimeSpan object to add or subtract time from DateTime objects."
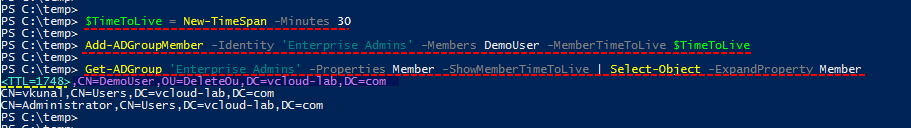
In next I have created small time span interval of 30 minutes, User will be part of domain for the period of time mentioned here.
$TimeToLive = New-TimeSpan -Minutes 30
In the next I am adding user account name Demouser in Group (Identity) Enterprise Admins using given timespan interval.
Add-ADGroupMember -Identity 'Enterprise Admins' -Members DemoUser -MemberTimeToLive $TimeToLive
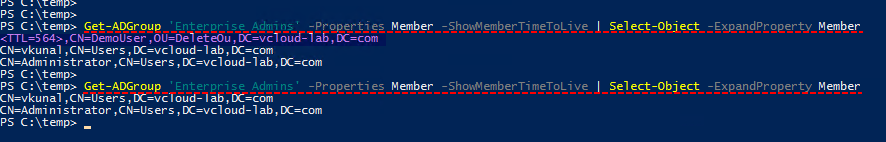
To identify the expiry time of user on the group use below one-liner. Check out the highlighted result It has extra property TTL and the value is in the seconds. Other permanent users don't have any TTL value.
Get-ADGroup 'Enterprise Admins' -Properties Member -ShowMemberTimeToLive | Select-Object -ExpandProperty Member
Keep running above command every few times and you will see the difference of decrease in TTL, time is reducing. Once the time expired user is automatically removed from group.
Note: When you add a new member to a group, the change needs to replicate to other domain controllers (DCs) in the bastion forest. Replication latency can impact the ability for users to access resources.
Below are the few use case for PAM.
- There’s no reason for all of users to have full access to every system, even if they are trusted.
- You have situations where a user needs escalated privileges, but only temporarily
- Your organization has strict compliance to mandates that you must follow.
- Managing privileged access is inefficient and requires too many resources.
- Group membership need to be rotated.
Userful Articles
Installing, importing and using any module in powershell
POWERSHELL: INSTALLING AND CONFIGURING ACTIVE DIRECTORY
Dynamic Objects
In Windows Server 2003 and later versions of Windows, Active Directory Domain Services provide support for storing dynamic entries in the directory. A dynamic entry is an object in the directory which has an associated time-to-live (TTL) value. The TTL for an entry is set when the entry is created. The time-to-live is automatically decremented, and when it expires the dynamic entry disappears. The client can cause a dynamic entry to remain longer than its current remaining life by refreshing (modifying) its TTL value. Clients that store dynamic data in the directory must periodically refresh that data to prevent it from disappearing.